Best Practices to Secure Your Organization
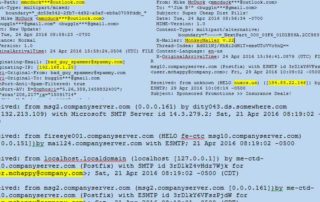
The current cyber threat landscape places business at a constant state of alarm. Businesses find themselves in a non-stop battle against viruses, Trojans, and hackers, some of which aim at stealing valuable intellectual property, while others just wreak havoc for the IT personnel and interrupt operations. However, not all threats are external to an organization. Some of the most damaging threats are those internal to a company, their own employees. Negligent employee disclosure of company proprietary information can have the most detrimental impact on the business. Whether an employee discloses valuable client information by accident, are working on company [...]