Cybersecurity Skilled Labor Shortage
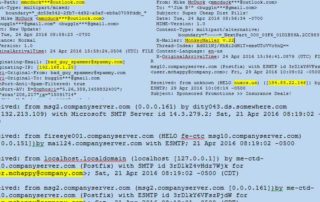
Alȳn Inc. has successfully provided value added Cybersecurity services to the Federal Government and Fortune 50 for over 10 years. With this experience and our battle-hardened, dedicated Cybersecurity expertise, we are expanding into the Commercial Sector. Through industry research and our experience working with top tier organizations, we have identified major gaps in the way organizations maintain their Cybersecurity structure and workflows, and have found rampant skilled labor shortages and confusion over role responsibilities. The teams most affected by these gaps are Incident Management, Digital Forensics, Threat Hunting, Threat Intelligence, and Big Data Analytics. These gaps are the result of [...]