Email headers contain important information about the origin and path an email took before arriving at its final destination, including the sender’s IP address, internet service provider, email client, and even location. The information could be used to block future emails from the sender (in the case of spam) or to determine the legitimacy of a suspicious email. A review of the headers can also help to identify “header spoofing,” a strong indication the email was sent with malicious intent.
Understanding the Header Fields
Email headers are read chronologically from the bottom up and can be broken down into three main categories: 1) Message Information 2) X-Headers and 3) Server Relay Information. There is a convenient tool for analyzing headers available online at http://mxtoolbox.com/EmailHeaders.aspx. Simply copy and paste the headers into the tool, and it will analyze the server relays and convert the headers into an easy to read format.
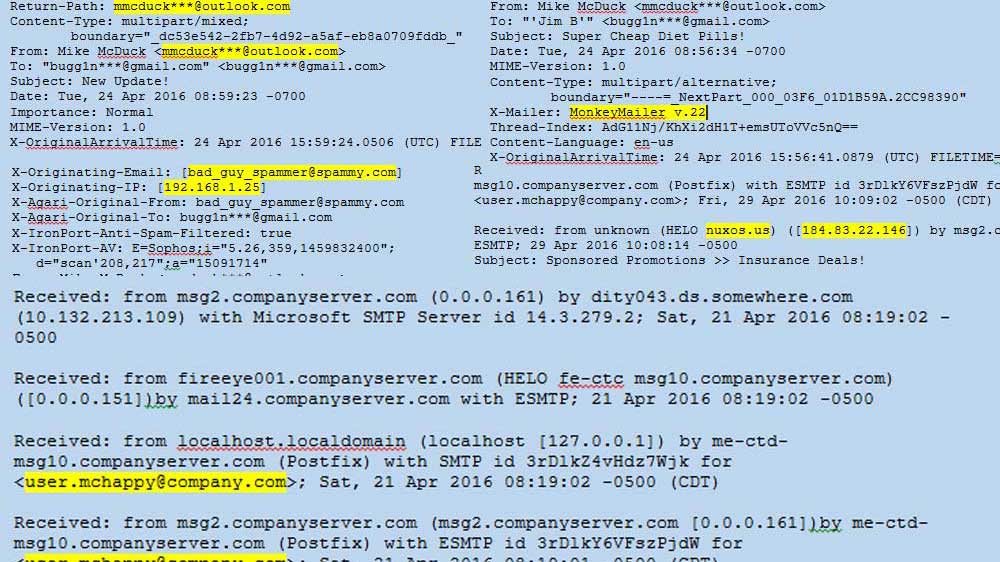
Message Information: Includes commonly recognized email header fields, such as To:, From:, Subject:, Date:, To:, as well as useful fields like Message-ID:, Return-Path:, ReplyTo:, among others. These fields are the most easily spoofed because they are specified by the sender’s mail client. They are usually found near the bottom of the headers as they are the first to be added.
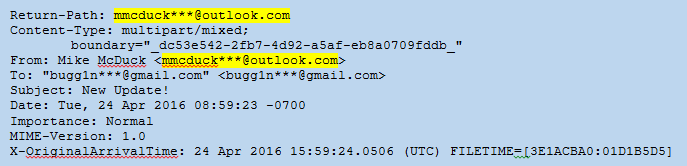
Figure 1: Headers – Message Info
X-Headers: These fields are added to the email by security devices such as email anti-virus scanners as it traverses the internet and internal networks. The X-Headers may not be in order and are often intermixed within the Message Info and Server Relay headers. Not all X-Headers will be present in every case. In the example below there is an X-Originating-Email: that reveals the true sender was bad_guy_spammer@spammy.com and not mmcduck***@outlook.com. Sometimes there is an X-Originating-IP as well. The headers below also show that the email was scanned by Agari Email Security and IronPort devices.
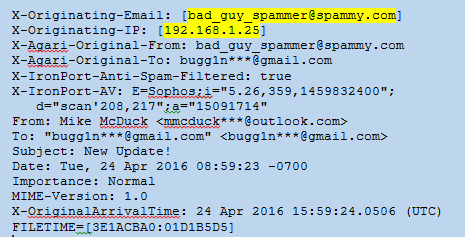
Figure 2: Headers – X-Headers
Server Relay Information: Each time a server relay receives an SMTP message, it will add a new Received: line at the beginning of the header block. A typical email received by a user on a corporate network will show many server relays both before and after being delivered to the corporate email servers (companyserver.com). These will be in chronological order starting from the bottom up.
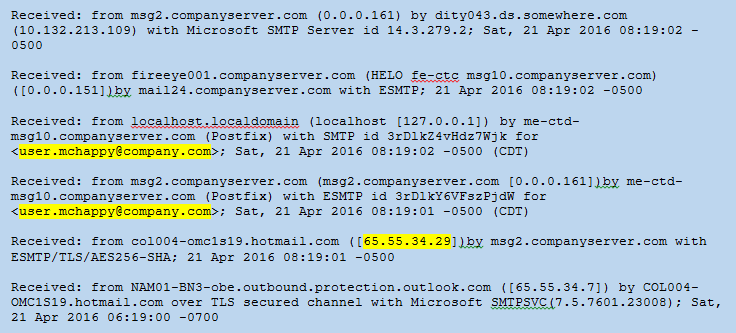
Figure 3: Headers: Server Relay
Analyzing Headers
By analyzing the server relay information in chronological order from the bottom-up, you can get a picture of where the message travelled. Each receiving mail server adds the name and IP address of the server that delivered the message. The server name may reveal the domain of the sender relay, and a Who-Is lookup of the IP may give you a geographic location. In the case of messages sent via Gmail and other large email service providers, this may only lead you back to the location of the email servers or even the corporate headquarters of the provider (i.e. Mountain View, CA). If you are lucky, the headers will include an X-Originating-IP that may reveal the sender’s internet service provider and narrow down the sender’s location.
If you are looking at spam email headers from a network security perspective, it is important to identify the IP address/domain that delivered the email to your frontline email server, the security device in front of your email server. This is called the “originating IP” (not the same as X-Originating-IP). It is the first field added to the headers that can be 100% trusted because it was added by your own security device/server. The server relay header will read “Received: from some.external.domain ([some.IP]) by your.company.device ([your.IP]).” Potentially, everything before this entry could be spoofed, but, as your server is reporting it received an email from some.external.domain ([some.IP]) and is the one adding it to the headers, you should be able to trust it. Once you know which external IP delivered the message, there is a free reputation service provided by Cisco at https://www.senderbase.org/. The service gives IP addresses and domains a reputation rating (Known spammer IP’s and domains received “Poor” reputations). The originating IPs can be blocked at the externally facing firewalls on a case by case basis, by reputation, or both. Figure 4 shows an email received by msg2.companyserver.com and the originating IP/domain is highlighted. Figure 5 shows the “Poor” rating the IP received from SenderBase.org.
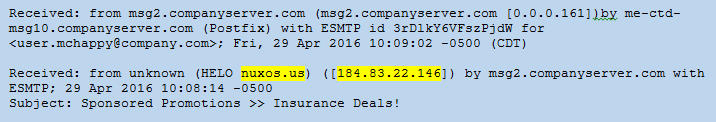
Figure 4: Headers – Originating IP
Figure 5: SenderBase.org – Reputation Rating
It is important to look for evidence of spoofing or alteration of header data in the Message Information headers. The spammer can easily alter these headers within their email client or by using specialized software. The most common field to spoof is the From: field. In the example in Figure 2, the sender changed the From: field to display “Mike McDuck <mmcduck***@outlook.com>” but the true sender was revealed by the X-Originating-Email field. It is not uncommon for spammers to use the recipient’s own name and email address in the From: field in order to increase the chances the recipient will open the email (“Why did I send this email to myself?”). The spammer will use any trick he or she can think of to deceive the recipient. Keep in mind the Return-Path: and Reply-To: can also be spoofed, depending on whether the spammer wants to receive the reply messages or not. Sometimes the To: field will also be altered to hide the intended recipient’s address.
The Message-ID is another good place to identify spoofing. The Message-ID is a unique identifier of digital messages and is difficult to alter as it is added by the mail server that processes the email. Because it has to be unique, it is common for message systems to use a date/time stamp followed by the sender’s domain name (example: CAF4Ths+hsd84G9sedaD@mail.gmail.com). If the sender domain in the From: field does not match the Message-ID, you might be dealing with a spoofed message.
The majority of spam emails are generated by servers capable of producing millions of messages per day. Sometimes those servers are running programs that populate the “X-Mailer” field with the name of the mail client that was used. Legitimate emails will usually include a known mail client (i.e. Microsoft Outlook 16.0, Outlook Express, iPad Mail), but the spammer mail clients may be something less common (see Figure 6) or even obscured through random, nonsense characters.
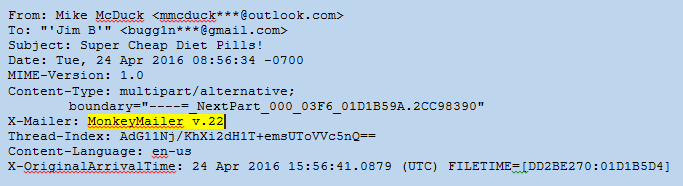
Figure 6: Headers – Mail Client
Now What?
At first glance, email headers can seem confusing and overwhelming. Once you begin to understand the fields in the headers and what they can reveal about the message, you will find very useful information buried in the seemingly endless lines of text. The next step will be determining what you can do with the evidence you find. Stay tuned to for future blog posts on using the headers to identify/block spam and to detect targeted phishing emails.